Introduced a long time ago, Windows Information Protection (WIP) still lives in a niche of configurations that only very few actually use. Which is a shame, as its very powerful and easy(-ish) to configure. You can read everything about it in Microsofts documentation for the feature.
One thing that was missing in a stringent security configuration, was the support for the new Edge browser. This changed this week with the release of version 81 in the stable channel. Let me show you how to adapt your WIP configuration to support the new Edge and deploy it with Microsoft Endpoint Manager f.k.a. Intune..
App Protection
For the scope of this post, I take it you have an existing WIP policy. If there is interest in going deeper into policies, let me know.
To let Edge access our corporate web resources, we have to add it to the allowed applications.
While Betas had to be added with a prepared XML file, the stable version is now natively supported in Intune. Just click “add” to get the selection of recommended apps:
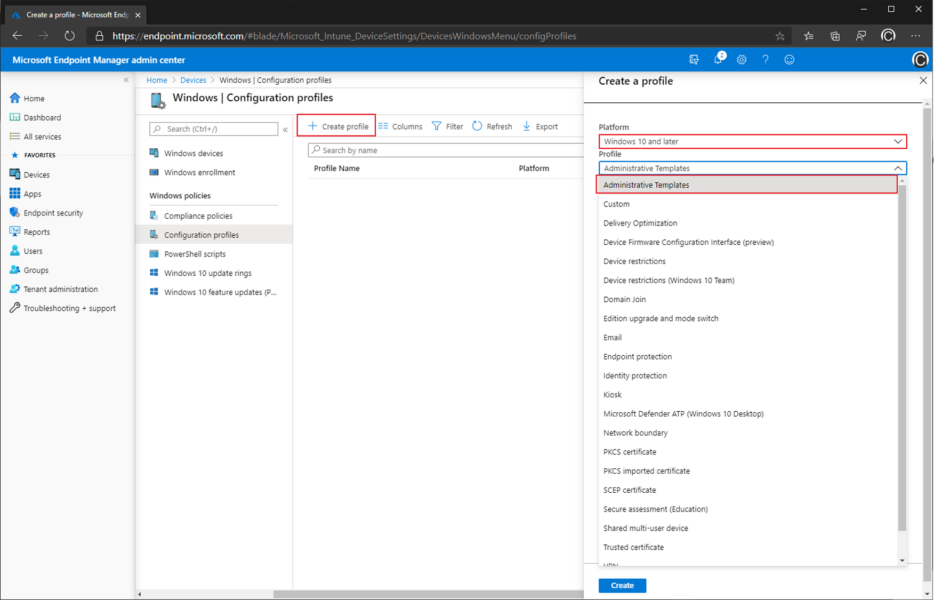
Give your policy a name and add a description. In the second step we need to choose a specific setting which is called “Enable Proactive Authentication” and add the policy “Enable a non-removable default sign-in profile” for added security.
In my case I allow pasting into personal applications as it is logged in the Windows Events log and I then ingest these logs in Azure Sentinel to alert the Security Operations Center. Something I will show you in my next post.
- Edge Version 81 now supports Windows Information Protection - April 14, 2020







2 Comments
Joe Mullarkey · June 27, 2020 at 18:23
Hi Philip,
I was trying to find a way through Intune to enable the “non-removable default sign-in profile” setting. I saw you mentioned it but you didn’t mention how to enable it with Intune. I know there is a way to do it via GPO, but I’m looking for an Intune method. Any thoughts?
Joe
Philip Büchler · July 28, 2020 at 09:40
Hi Joe
Intune can set it through a Device Configuration policy where you set “Browser Sign-In Settings” to “force users to sign-in to use the browser” within an administrative template.
Does that answer your question?
Cheers Philip