Windows 10 auditing needs to be configured to comply with the Microsoft Security Baseline. In my opinion this is an important part but completely missed in the Intune UI. But happily there is the Policy CSP which allows us to configure it. The CSP is documented here https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-audit.
To simplify the process for you, I created a table with the correct OMA-URI’s and values. You can start by creating a custom Configuration Profile in Intune:
Then create for each item from the table bellow an entry. The name can be any value, but I recommend using the “Policy Setting Name” from my table. The data type has to be “Integer” and the value can be copied from the “Integer value” column.
The following table lists all audit log settings to comply with the Microsoft Security Baseline:
| Policy Setting Name | Value Readable |
OMA Uri |
Integer Value |
| Audit Credential Validation | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/AccountLogon_AuditCredentialValidation |
3 |
| Audit Security Group Management | Success |
./Vendor/MSFT/Policy/Config/Audit/AccountManagement_AuditSecurityGroupManagement |
1 |
| Audit User Account Management | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/AccountManagement_AuditUserAccountManagement |
3 |
| Audit PNP Activity | Success |
./Vendor/MSFT/Policy/Config/Audit/DetailedTracking_AuditPNPActivity |
1 |
| Audit Process Creation | Success |
./Vendor/MSFT/Policy/Config/Audit/DetailedTracking_AuditProcessCreation |
1 |
| Audit Account Lockout | Failure |
./Vendor/MSFT/Policy/Config/Audit/AccountLogonLogoff_AuditAccountLockout |
2 |
| Audit Group Membership | Success |
./Vendor/MSFT/Policy/Config/Audit/AccountLogonLogoff_AuditGroupMembership |
1 |
| Audit Logon | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/AccountLogonLogoff_AuditLogon |
3 |
| Audit Other Logon/Logoff Events | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/AccountLogonLogoff_AuditOtherLogonLogoffEvents |
3 |
| Audit Special Logon | Success |
./Vendor/MSFT/Policy/Config/Audit/AccountLogonLogoff_AuditSpecialLogon |
1 |
| Audit Detailed File Share | Failure |
./Vendor/MSFT/Policy/Config/Audit/ObjectAccess_AuditDetailedFileShare |
2 |
| Audit File Share | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/ObjectAccess_AuditFileShare |
3 |
| Audit Other Object Access Events | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/ObjectAccess_AuditOtherObjectAccessEvents |
3 |
| Audit Removable Storage | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/ObjectAccess_AuditRemovableStorage |
3 |
| Audit Audit Policy Change | Success |
./Vendor/MSFT/Policy/Config/Audit/PolicyChange_AuditPolicyChange |
1 |
| Audit Authentication Policy Change | Success |
./Vendor/MSFT/Policy/Config/Audit/PolicyChange_AuditAuthenticationPolicyChange |
1 |
| Audit MPSSVC Rule-Level Policy Change | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/PolicyChange_AuditMPSSVCRuleLevelPolicyChange |
3 |
| Audit Other Policy Change Events | Failure |
./Vendor/MSFT/Policy/Config/Audit/PolicyChange_AuditOtherPolicyChangeEvents |
2 |
| Audit Sensitive Privilege Use | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/PrivilegeUse_AuditSensitivePrivilegeUse |
3 |
| Audit Other System Events | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/System_AuditOtherSystemEvents |
3 |
| Audit Security State Change | Success |
./Vendor/MSFT/Policy/Config/Audit/System_AuditSecurityStateChange |
1 |
| Audit Security System Extension | Success |
./Vendor/MSFT/Policy/Config/Audit/System_AuditSecuritySystemExtension |
1 |
| Audit System Integrity | Success and Failure |
./Vendor/MSFT/Policy/Config/Audit/System_AuditSystemIntegrity |
3 |
As soon you added all settings to the profile you can save and assign it to your devices.
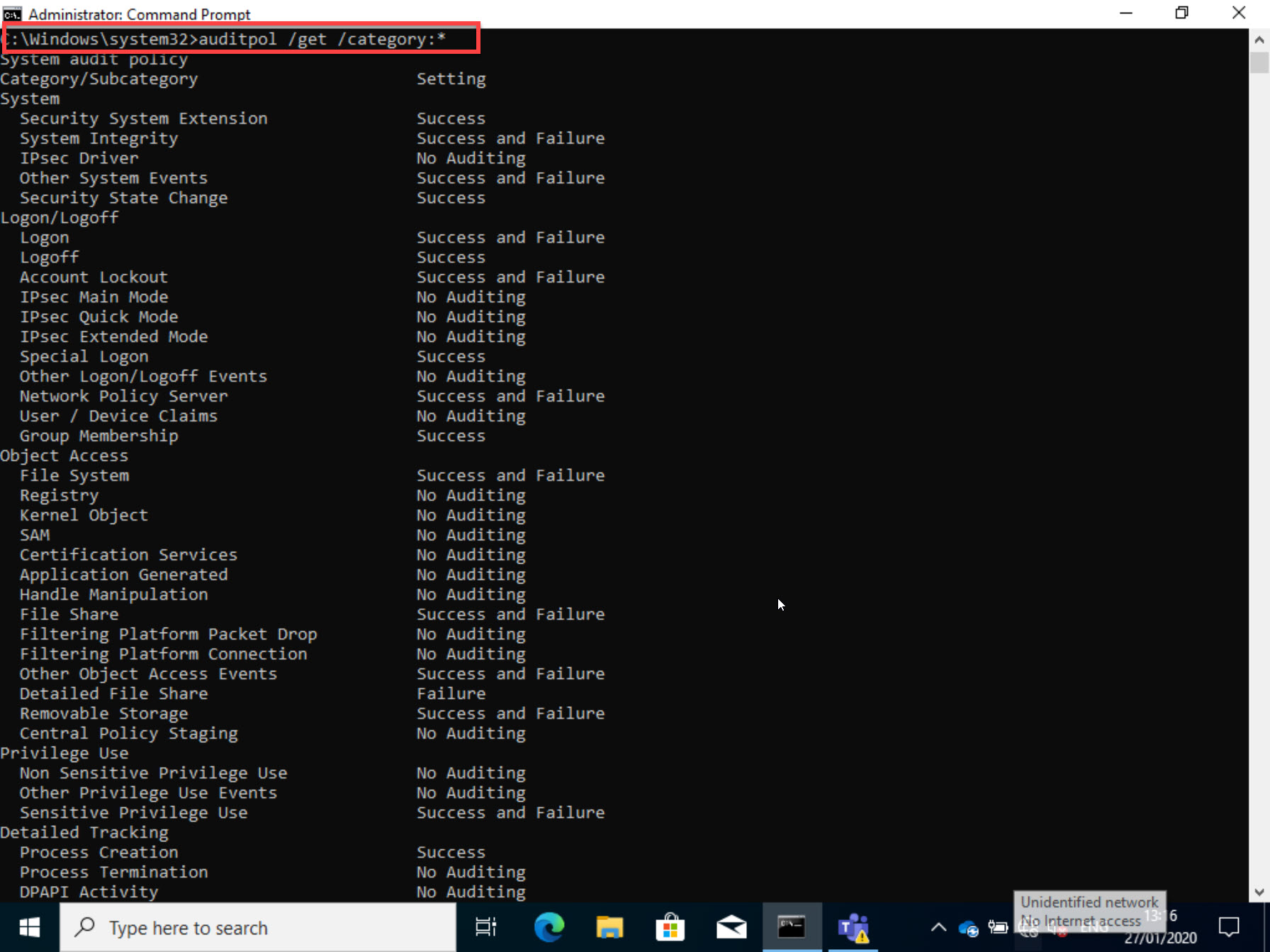
Result
After deploying the profile it is important to check if it is really applied on the devices. The easiest way is to do it with the following command:
auditpol /get /category:*
- Microsoft Sentinel ASIM Parser demystified - March 31, 2024
- Enhancing Network Security Insights with IDS/IPS of Ubiquiti Dream Machine Pro and Microsoft Sentinel - March 10, 2024
- Ubiquiti Dream Machine Pro Logs to Microsoft Sentinel - February 6, 2024






14 Comments
Nilldot · May 13, 2020 at 21:44
This is very much appreciated. Thank you!
Sol · August 23, 2020 at 20:13
Thank you! This was great
Jason · December 12, 2020 at 01:21
If you notice in your cmd line results, not all the policies are being correctly set. For instance “Audit Other Logon/Logoff Events”. In my case I’ve tried to apply the new MDM Security Baseline for August 2020 and I’m getting errors for a whole bunch of the audit settings and they aren’t being applied. No idea why because everything looks correct. I bet I’m not the only one.
Thomas Kurth · January 1, 2021 at 15:28
I had the same at a customer. It depends on the Windows version you have. For example 1809 and older is not working… despite it should according to Microsoft documentation.
KV · February 20, 2021 at 20:06
Hi Thomas, Thank you for creating the blog, I too noticed that I get a bunch of errors my Windows Version is 19042.804 . Do you perhaps have a solution for this ?
Thomas Kurth · March 1, 2021 at 14:42
Strange, now until now it worked without any issues on newer Windows versions. What error messages do you see?
Power Test · March 9, 2021 at 06:19
Hello Thomas,
Thanks so much for putting this together! I really appreciate it. It saved me a lot of time!
I found that after assigning this profile to my test machine that “Other Logon/Logoff Events” kept showing “No Auditing”. I tried changing some other auditing values, after syncing my test machine from intune, those would update correctly. Then I came back to your page and saw that in your screenshot, “Other Logon/Logoff” is set to “No Auditing” as well. Its supposed to be set to “Success and Failure”, correct? Am I reading the cmd prompt output wrong?
Power Test · March 9, 2021 at 06:57
Thomas, I discovered the error and it appears to be a microsoft mapping error.
It looks like the OMA-URI AccountLogonLogoff_AuditOtherLogonLogoffEvents triggers a change in the audit status(as reported from the cmd line auditpol cmd) of the policy for the Account Logon -> Other Account Logon Events – which should be OMA-URI Audit/AccountLogon_AuditOtherAccountLogonEvents.
I tried setting the Audit/AccountLogon_AuditOtherAccountLogonEvents to “3” to see if they had been switched. Unfortunately, Logon/Logoff -> Other Logon/Logoff Events still shows “No Auditing” from the command line after a successful sync and audit change on other settings.
I’m sort of disheartened by this. I’m new to InTune and Endpoint Manager. I found an error in the security baseline and asked Microsoft about it. They said that errors happen sometimes with thousands of settings to check. That’s why they’re implementing the Settings Catalog. It should remove the transcoding issues. However, this was a custom OMA-URI setting. This should map to the correct policy.
I am not exhaustively testing this stuff. This is the first stuff I’m getting my hands dirty with and I’ve already found these errors. How are they getting by Microsoft quality control?
Power Test · March 10, 2021 at 04:32
As described above, I set “Audit/AccountLogon_AuditOtherAccountLogonEvents to “3” and now that policy is showing a configuration error in intune “-2016281112 (Remediation Failed)” So, that CSP isn’t working as it should – probably because of the conflict with the mis-mapping of AccountLogonLogoff_AuditOtherLogonLogoffEvents.
Thomas Kurth · April 25, 2021 at 19:39
Sadly I tested this as well and nothing is working. So, I assume its an issue in Windows because the CSP’s are provided by the OS.
Barker · July 2, 2021 at 15:58
Thomas, This was extremely helpful. You ROCK!
Tanvi · November 26, 2021 at 09:35
Hi Thomas, Thanks for this amazing post. Really appreciate all of your efforts.
How to view these audit logs in intune. For my organization I need to monitor the file copied to and from removable storage. Thanks in advance.
Thomas Kurth · January 28, 2022 at 22:18
Hello Tanvi
The Audit logs are written to the Windows Event Log, not to Intune. The solution you search is Microsoft Endpoint DLP.
Samael Ambrona · February 17, 2022 at 16:41
Thank you for the information Thomas, it is really helpful.
I have a question though. On the GPO where we have defined the Logon / Logoff audits, we have also “Audit Logon Events” configured to “Failure”. How can I translate it to CSP? For more that I read, I cannot find the way.
Best regards